CSE 4380.010 Information Security
CSE 4380/5380 is a technical elective Computer Science and Engineering course at the University of Texas at Arlington that explores the fundamentals of information security.
Upon successful completion of this course, students will be able to:
- Use cryptographic primitives directly in order to understand their respective uses and how they work together to provide security.
- Develop simple malware in order to understand hooking and how hooking can be subverted for malicious purposes.
- Set up and use defensive and security testing technologies in the network and operating system in order to see how they defend against attacks.
- Exploit software vulnerabilities in order to understand how they work and how defenses could stop them.
- Study a range of concepts to gain a broad understanding of the field of information security.
- Apply class knowledge in a capture-the-flag simulation exercise at the end of the semester.
Info
Class Information
- Lecture
- Section 010 Fri 1:00 PM - 3:50 PM
- Location
- WH 221
- Course Syllabus
- Section 010: 1:00pm - 3:50PM
- Zoom Meeting
- 268 571 9880
- Slack
- cse4380.slack.com
- GitHub
- CSE4380 Fall 2025
Instructor
- Instructor
- Trevor Bakker (trevor.bakker@uta.edu)
- Office Hours
- Friday 8:30 AM - 11:30 PM, and by appointment
- Office Location
- 321 Engineering Research Building
Help Protocol
- Think
- Slack
- Think
- Think
- Office Hours
Teaching Assistants
- Teaching Assistant
- Tong Chen (txc5603@mavs.uta.edu)
Office Hours
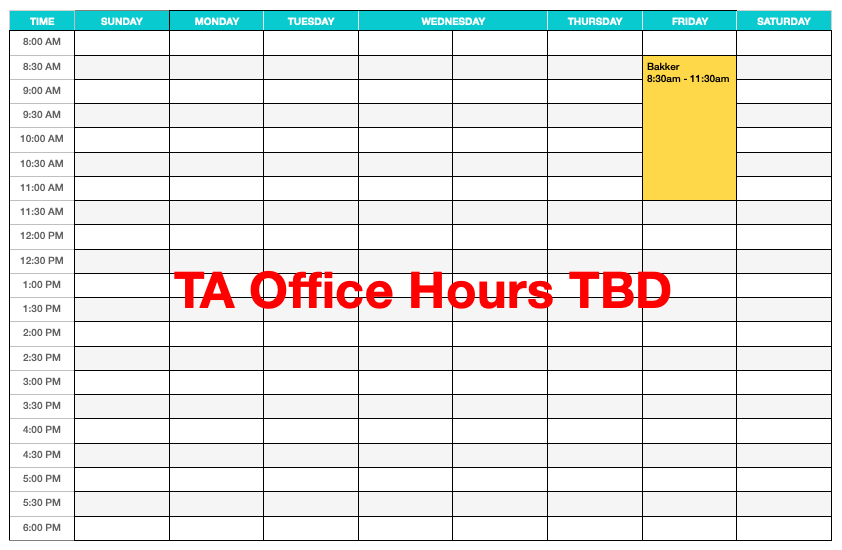
Online Office Hours
Online office hours will take place in Zoom Meeting 268 571 9880. Please use the main session for general questions. If you have an individual question, then request a private breakout room.
If you need more individualized attention, please contact the instructor to schedule an appointment.
Schedule
| Date | Topics | Assigned | Lab | Project |
|---|---|---|---|---|
| Week 1 - Fri 08/22 | No Class | |||
| Week 2 - Fri 08/29 | Introduction, Chapter 2 and 20 - Encryption | Pre-lab 1 | ||
| Week 3 - Fri 09/05 | Chapter 13 - Trusted Computing | |||
| Week 4 - Fri 09/12 | Chapter 14 - IT Security Management and Risk Assessment | Pre-lab 2 | Lab 1 | System Categorization Assigned |
| Week 5 - Fri 09/19 | Chapter 15 - IT Security Control, Plans, and Procedures | |||
| Week 6 - Fri 09/26 | Chapter 3 - Access Control and Chapter 4 - Access Control | Lab 2.1 | ||
| Week 7 - Fri 10/03 | Chaper 6 - Malicious Software and Chapter 7 - Denial-of-Service | Lab 2.2 | Security Control Selection, Attack Trees, Risk Assessment & Mitigation | |
| Week 8 - Fri 10/10 | Mid-Term Exam | |||
| Week 9 - Fri 10/17 | Chapter 8 - Intrusion Detection and Chapter 9 - Firewalls | Pre-lab 3 | Cybersecurity Strategy Implementation Plan | |
| Week 10 - Fri 10/24 | Chapter 10 - Buffer Overflow and Chapter 11 - Software Security | Pre-lab 4 | ||
| Week 11 - Fri 10/31 | Chapter 12 OS Security and Chapter 13 - Trusted Computing | Lab 3 | ||
| Week 12 - Fri 11/07 | Chapter 16 - Physical Security and Chapter 17 - Human Resources | Lab 4.1 | ||
| Week 13 - Fri 11/14 | Chapter 19 - Legal and Ethical Aspects | Pre-CTF | Lab 4.2 | System Security Plan and ATO Package |
| Week 14 - Fri 11/21 | TBD | CTF | ||
| Week 15 - No Class (Thanksgiving Holiday) | ||||
| Fri 12/05 | Final Exam |
Requirements
4380 Coursework
| Component | Points |
|---|---|
| Labs Labs | ( Prelabs 2% + Labs 3% ) * 5 Labs) = 25% |
| Project Labs | 25% |
| Mid-Term Mid-Term Exam. | 25% |
| Final Exam | 25% |
Grading
| Grade | Average |
|---|---|
| A | 90-100 |
| B | 80-89 |
| C | 70-79 |
| D | 60-69 |
| F | 0-59 |
Policies
Guide to the Honor Code
For the assignments in this class, you may discuss with other students and consult printed and online resources. You may not quote from books and online sources. You may not look at another student's solution, and you may not copy any portions of other's solutions. Furthermore, you may not utilize AI powered tools such as Co-Pilot, Tabnine, or ChatGPT for any of your programming assignments.
The following table summarizes how you may work with other students and use print/online sources:
| Resources | Solutions | AI Tools | |
|---|---|---|---|
| Consulting | Allowed | Not Allowed | Not Allowed |
| Copying | Not Allowed | Not Allowed | Not Allowed |